Gone are the days when you would send an email and not have to worry about it getting delivered. SPAM has been around for almost as long as email and receivers today have quite a job deciding what is real and what’s not. Wouldn’t it be great if legitimate senders had a clever way of helping them accomplish this? If there was only something we could do to help our email hit the Inbox and separate us from the junk. Well, keep reading because that’s exactly what Email Authentication is all about.
Authentication prevents spammers from using your domain to send emails without your permission. There are 3 main protocols in use today (SPF, DKIM, DMARC, and BIMI) and each helps validate your email is legitimate in an effort to help maximize your delivery.
Sender Policy Framework (SPF) is an authentication standard that has been around since 2003 and works by publishing a list of servers (IP address or Domain Name) that are authorized to send email on behalf of a domain. Receiving mail servers will use SPF to verify that messages sent from your domain were sent by one of these IP addresses. SPF authenticates the Return-Path: domain with the IP address used to send the email.
SPF helps protect your domain against spoofing and helps prevent your outgoing messages from being marked as spam by receiving servers. Whether the SPF passes (or fails) can be seen in the Authentication-Results: header. However, this only validates the server sending the email; it does not ensure that the content has not been tampered with. For that, we need DKIM (Domain Keys Identified Mail).
DKIM stands for DomainKeys Identified Mail and is a complex method of authentication that encrypts the email in transit by signing it with a digital signature which creates a unique string of characters called a “hash value.” When a receiver detects an email has been signed using DKIM, it will authenticate the message using a pair of “keys” :
1st key – “Private Key” is kept safe by the sender and cannot be shared.
2nd key – “Public Key” is stored in the DNS of the client’s From domain.
When the email is received, the receiver will use these keys to decrypt the hash value in the
header and if both keys match, it shows the email has not been altered and the DKIM signature is then verified. If the keys do not match, the DKIM signature will fail and the recipient’s ISP will be more likely to place the email in the Spam box or block it outright. DKIM — which is a method of adding a tamper-proof domain seal to a piece of email — has roots going back to 2005.
But how can I see who is using my domain without my permission? Enter DMARC.
DMARC stands for Domain-based Message Authentication, Reporting & Conformance and it’s a standard that mail servers use to determine if an incoming email is coming from sources that the domain sending the email trusts.
DMARC uses SPF or DKIM to verify if the sender is genuine and takes authentication one step further by sending a report of who is using their domain back to the sender. For DMARC to pass, the email must pass either SPF or DKIM, and the domain in the From header must be aligned with the corresponding SPF or DKIM domain.
The main advantage of DMARC is that it’s the sender who controls what happens to spam sent using their domain, not the receiver. So you can tell the receiver to block mail you didn’t send, and better yet, you get a report of mail that is using your domain without your permission – so DMARC is very powerful and is the gold standard in use today.
As the DMARC record is setup, our managed DMARC solution will start to get flooded with XML reports telling you who is using your domain. These reports provide insight into how your email is moving through the ecosystem and allow you to identify if anyone else is using your domain. Making sense of these reports can be tricky and they can be numerous. Not only can can we help create your DMARC record with ease, but our platform can also be used to view these XML reports and provide visualization on how your email domains are being used so you can take action. You will need this visibility in order to ensure you do not block legitimate mail before moving your DMARC policy towards p=quarantine or p=reject.
DMARC is the technology of Domain-based Message Authentication, Reporting and Conformance. DMARC brings new features to the world of email, and is aimed squarely at solving a problem that has plagued email from the very beginning. This problem is related to having a reliable way to tell if email is real or just a really good fake.
Instead of relying on a single technology, DMARC brings consistency to how these existing technologies are configured so that when a piece of email is received, a simple check can be performed to see if the email really does come from the domain it says it comes from.
The goal is to make email easy to identify, but this isn’t very useful unless all of a domain’s email can be identified. If it’s easy to identify only some of a domain’s email, then people still have to go to great lengths to figure out if the remaining parts are real or if they just look real but are in fact phishing emails that end up causing a lot of grief.
To make it so that all of a domain’s email can be made easily identifiable, DMARC gives domain owners visibility into how their Domains are being used on the Internet. This visibility comes in the form of feedback reports that are generated by organizations that process incoming mail. The reports are sent to domain owners when they ask for them. By analyzing these reports, domain owners can identify all of their sources of email, which makes it possible to deploy the underlying technologies across all legitimate email streams. Without these reports, a domain owner would have to somehow audit their organization to figure out who all is sending email — a task that is time consuming and almost guaranteed to be incomplete. With these reports a domain owner can get the work done quickly and accurately.
To tie this all together, when a Domain owner is confident that they’ve made all of their legitimate email easy to identify, they can tell the world to block the fake stuff. Today, DMARC is used to block a lot of fake email, which is a very good thing.
However, even though blocking fake email is great, the visibility that DMARC provides to Domain owners is useful in itself. People use DMARC to see if their domains are being abused on the Internet. Organizations use DMARC to understand how they and their partners are sending email using their domains, and also if everyone is sending email correctly. Doing this turns DMARC into a compliance tool that organizations use to make sure they’re doing everything they can to reduce the risk of fraud to themselves and their customers and also to make sure that any liability in terms of adhering to best practices to protect users and assets is reduced.
Arguably the best thing that DMARC is doing for email is to change email from a “lets keep the bad stuff out” model to a “lets build on our ability to identify real email.” Receivers of email are radically simplifying how they process email, even to the point of requiring DMARC compliant email if you’re trying deliver a lot of email.. and this is a pretty big deal to any organization that relies on email for its day to day business.
What started with a small list of ISPs like AOL, Yahoo, and Gmail, has grown into a long list around the world with more and more being added every day. Here is a current list of known receivers checking for DMARC:
|
Amazon WorkMail AOL Apple ATT BT Mail Cisco Email Security Comcast Gmail Google Apps Hotmail Hover |
LaPoste Libero.it Mail.ru Mimecast Office 365 Onet Proofpoint Rackspace Rogers SFR Shaw |
Skynet Proximus Sophos SpamExperts Symantec Vade Secure Yahoo! Yahoo! UK Ziggo Zoho |
The time to set up DMARC and secure your domain is now!
If an email is valid, a BIMI Record, a particular DNS Record, is used to display a firm logo inside the inbox. An industry-wide initiative called Brand Indicator Message Identification (BIMI) Records aims to employ brand logos as indications to help email recipients spot and avoid fake messages. Only a few Oath brands (Yahoo!, AOL, etc.) are now testing this standard in front of their mailbox subscribers, making it still in beta.
If this standard is fully implemented, it should benefit both companies that send emails and all individual email users. When phishing/spam emails masquerading as business communications arrive in email inboxes, email users will have a reliable way to visually identify them. Businesses will also gain the following advantages with BIMI record generator:
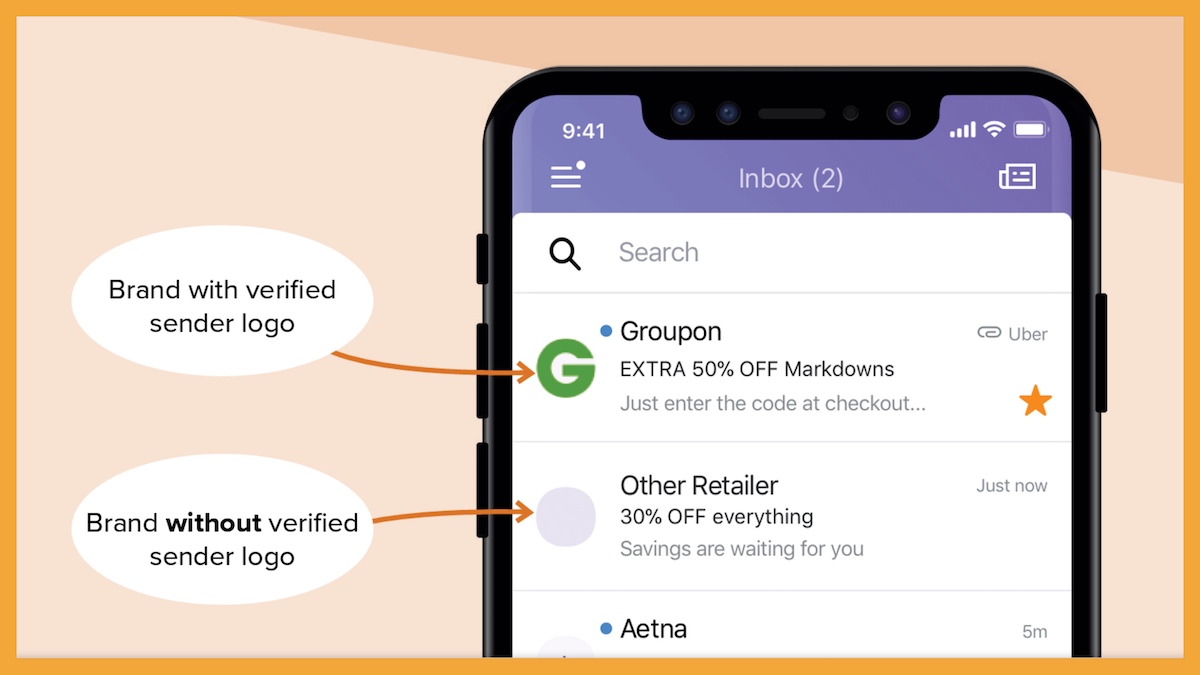
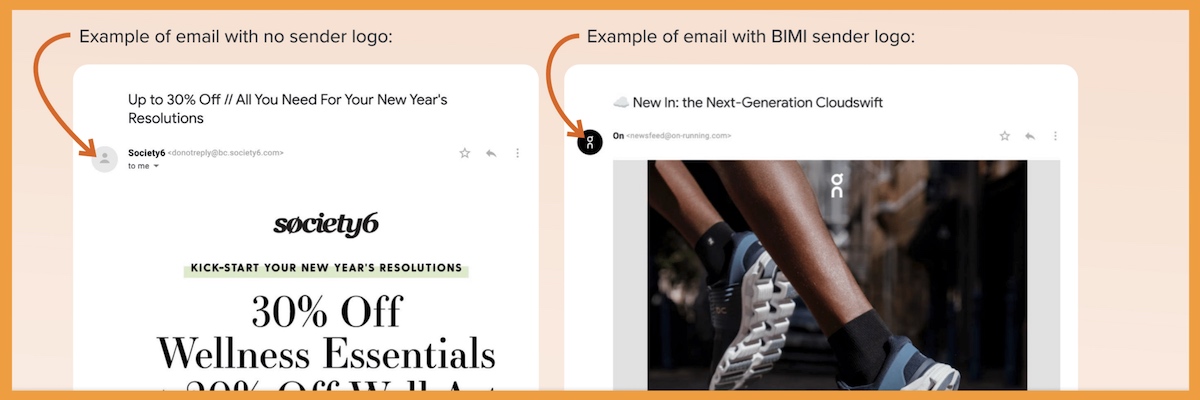
BIMI support includes several major inbox service providers (ISP)—like Gmail, and Verizon Media Group (Yahoo, AOL, Netscape). But in June 2022, there was an update: Apple Mail was added to the list. Its developer support page explains how they will support BIMI and which OSs will be supported.
Here’s a list of BIMI support by mailbox provider, as of July 2022:

Here are the mailbox providers that currently support BIMI:
Mailbox providers considering BIMI include:
Sources: What Is BIMI (And Why Should Email Marketers Care?) – Litmus , Why Is BIMI important in Email Marketing? (linkedin.com) , Authenticating my domain with SPF, DKIM and DMARC protocols – Support (cakemail.com)
344 N. Washington Street
Saint Croix Falls, WI 54024
Hours: Mon-Fri, 10AM to 6PM
24/7/365 – Business Premium Partners ONLY