
Improve Your Workplace Productivity With Microsoft Word: 11 Tips To Make the Most of This Program
Microsoft Word is an indispensable part of most business environments. It has numerous features that
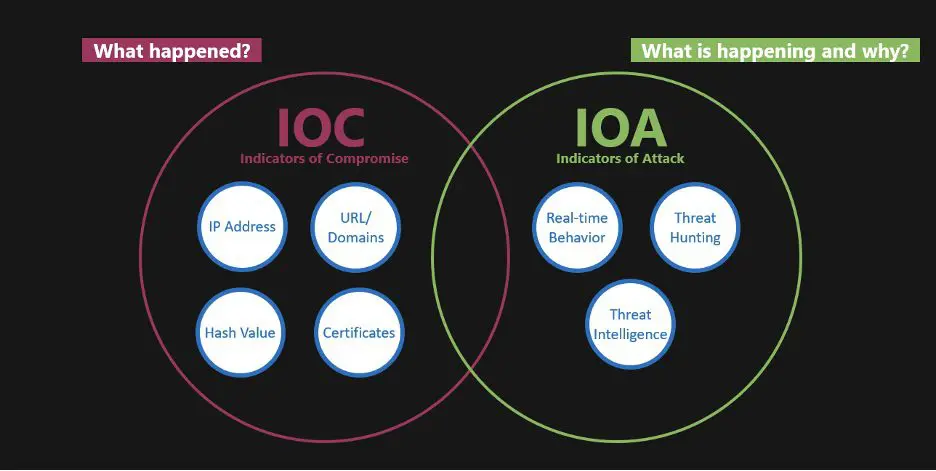
Indicators of Compromise (IOCs) are digital clues that suggest a network or endpoint may have been breached, serving as crucial evidence in cybersecurity. They are used by information security professionals to detect malicious activities, including malware attacks and data breaches. IOCs can be identified manually or through automated systems, aiding in mitigating ongoing attacks and improving future security measures. However, the effectiveness of IOCs is challenged by the evolving sophistication of cybercriminals, making detection increasingly difficult.
Unfortunately, IOC monitoring is reactive in nature, which means that if an organization finds an indicator, it is almost certain that they have already been compromised. That said, if the event is in-progress, the quick detection of an IOC could help contain attacks earlier in the attack lifecycle, thus limiting their impact to the business.
When a hacker tries to attack or successfully attacks an organization, they often leave digital footprints or clues in the organization’s computer systems and logs. A specialized team within the organization, known as the threat hunting team, looks for these clues to figure out if there has been a security issue or if one is currently happening.
Who Identifies These Signs?
The job of spotting these signs, known as Indicators of Compromise (IOCs), is usually done by trained cybersecurity professionals. They use sophisticated tools to examine a lot of data moving through the organization’s networks to find any suspicious activities. A threat hunting team is generally responsible for monitoring and alerting of IOCs and IOAs.
Why It’s Important to Look for These Signs
Detecting IOCs is vital for any organization’s cybersecurity plan. Recognizing these signs early can help reduce the damage of an attack and make it easier to fix the problem. These indicators also give insights into the methods used by attackers, helping organizations improve their security measures and prevent future attacks.
Examples of These Signs
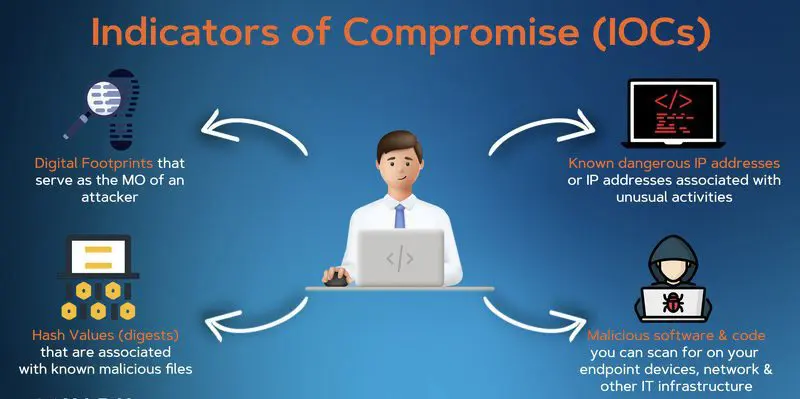
Some common signs that the security team looks for include:
– Unusual data traffic coming in or going out.
– Traffic from unexpected places.
– Strange applications found on the system.
– Suspicious activities from high-level user accounts.
– Repeated failed login attempts.
– Sudden increase in database access.
– Many requests for the same file.
– Changes to system files or settings that weren’t authorized.
The Difference Between IOCs and Indicators of Attack (IoAs)
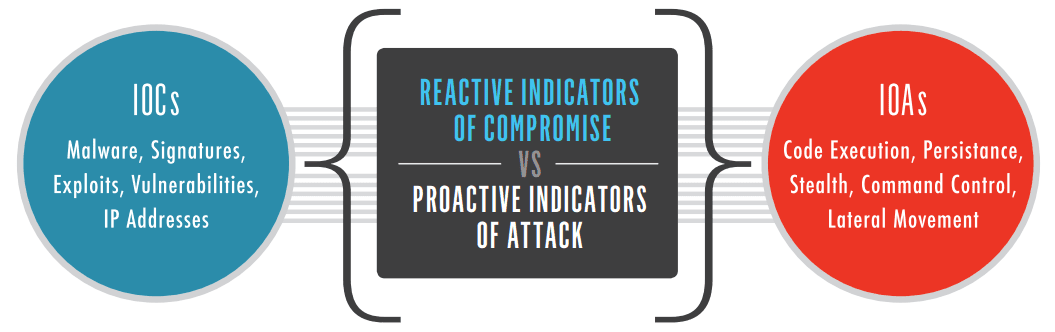
While IOCs help identify that a cybersecurity event has happened or is happening by looking at the aftermath, Indicators of Attack (IoAs) are about spotting an ongoing attack. They focus more on understanding the attacker’s actions and goals, unlike IOCs, which are more about recognizing that an incident occurred.
Subscribe to get the latest posts sent to your email.

Microsoft Word is an indispensable part of most business environments. It has numerous features that

Your business can benefit a lot from working with an IT provider. However, you need

Making the most of your Microsoft 365 apps requires you to adopt appropriate security measures.Microsoft

You may have state-of-the-art servers, but their efficiency can diminish over time. Managing them is
Subscribe now to keep reading and get access to the full archive.