A client business email account was compromised and the attacker sent emails to everyone in his contact list… he also read all of his entails… logged in easily as the client… learned his email style… searching through the info for sensitive info they can use in the attack… and… this email did not have MFA and likely was using a simple and very old password. Completely avoidable with basic MFA and a password manager. This client should also get identity protection for himself and his family as a proactive step. He is retired and is a multi-business owner.
Here is what it looks like:
Step 1: Send email to all contacts as trusted person. Make it look legit and important. Before doing so, look at all emails and choose highest likelihood of success. If a business, pick a business template and send.
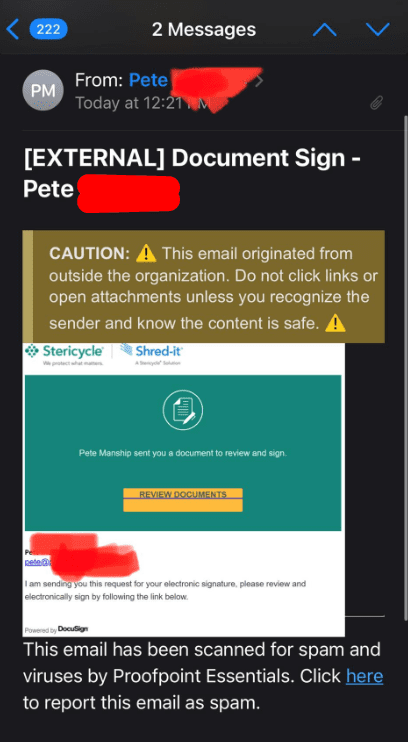

Step 2: create fake Google site with link to document that needs to be downloaded. Either infect system with drive by or timeless or zero day download. Or choose phishing method to catch passwords. Password phishing test chosen…
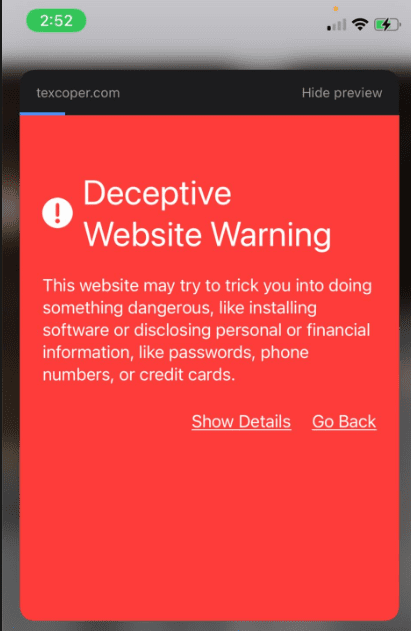
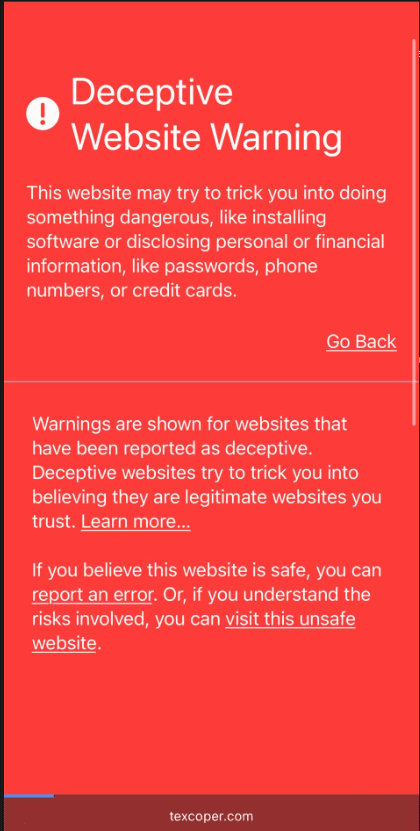
Step 3: Click link… if protection systems in place, protection will warn other users. If not, let the phishing begin… Warnings would look like…
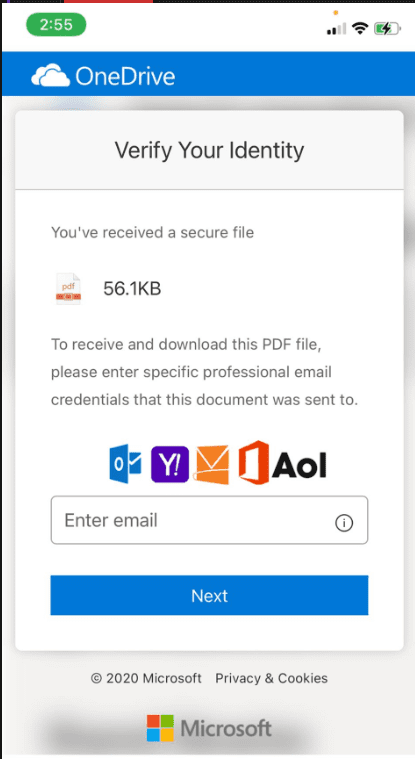
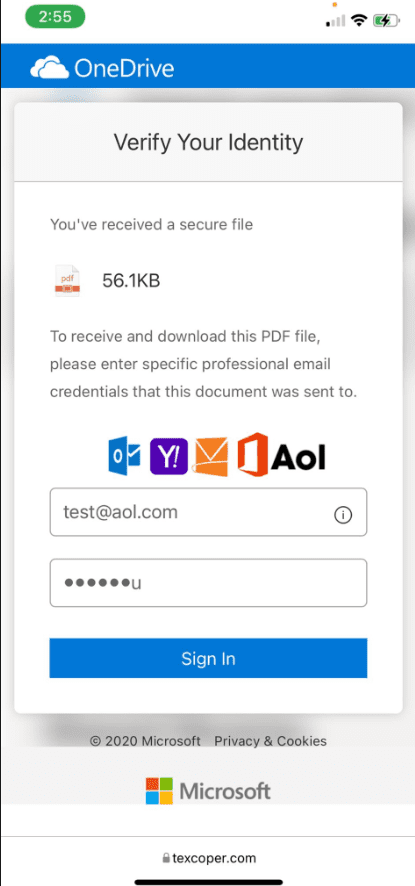
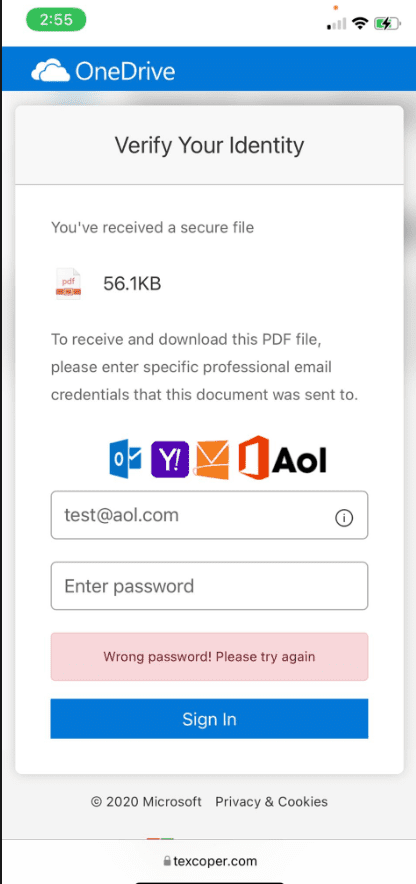
If warnings are bypassed, then the actual phishing page looks like this:
Step 4: Get end user to provide every password they know for all of their emails and accounts. They will continue to do this until they give up. Great way to get a LOT of information without direct hacking.
Step 5: Find end user accounts in email. Try all passwords. Get money In Whatever way possible. Continue to target and attack. Put on easy target list. Try bank accounts and other systems. Look for personal information. Look for credit cards, social security numbers, anything that can be used to hijack accounts and get money.
Rinse and repeat for any and all contacts that fill out phishing page. Continue attack forever until you are swimming in money. Screw America. Screw these end users. If they don’t know how to protect themselves or their money, then I deserve it. It’s mine, so a better job. Maybe you will learn a lesson from this. I’m actually helping you. You’re welcome!
Pro tip #1: This email passed all checks and security because it’s an actual legit email from a client using their account. Keep that in mind!!!
Pro tip #2: After verifying email account is secure with new password and MFA has been enabled, be sure to inspect webmail settings. In this instance the attacker had created a custom outlook rule that was instantly moving and deleting new email messages.
Discover more from EasyITGuys #
Subscribe to get the latest posts sent to your email.